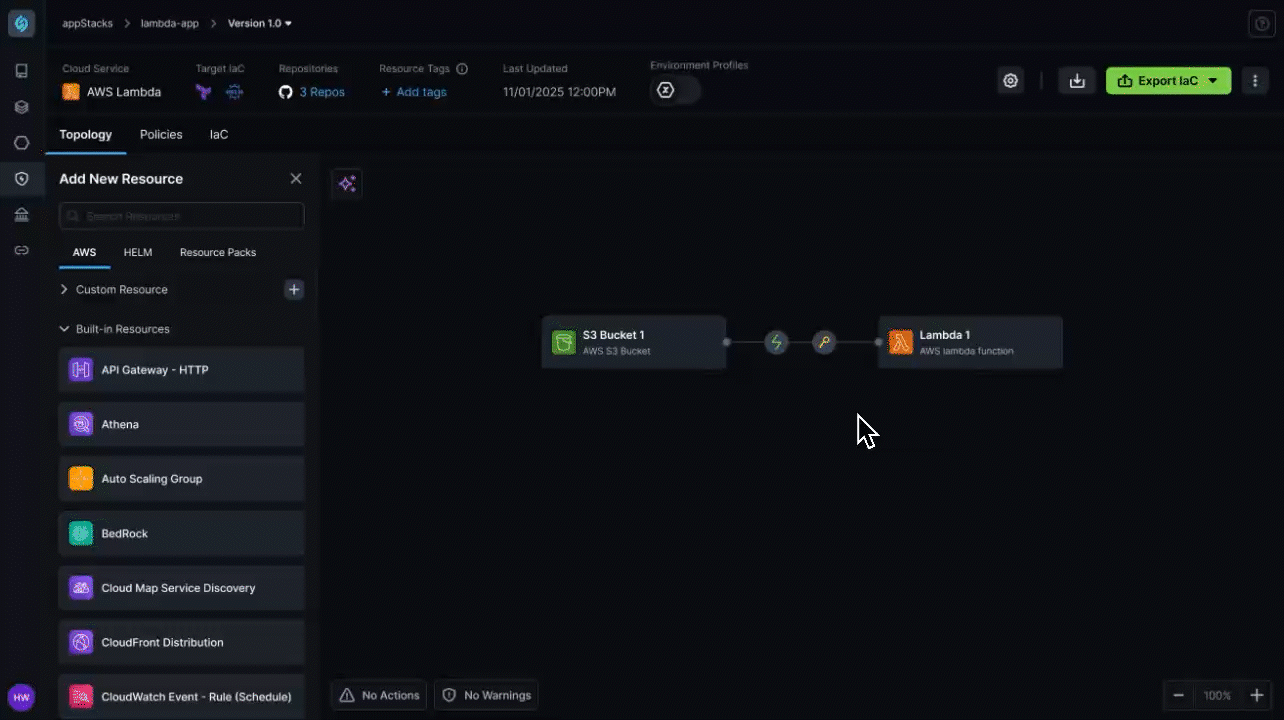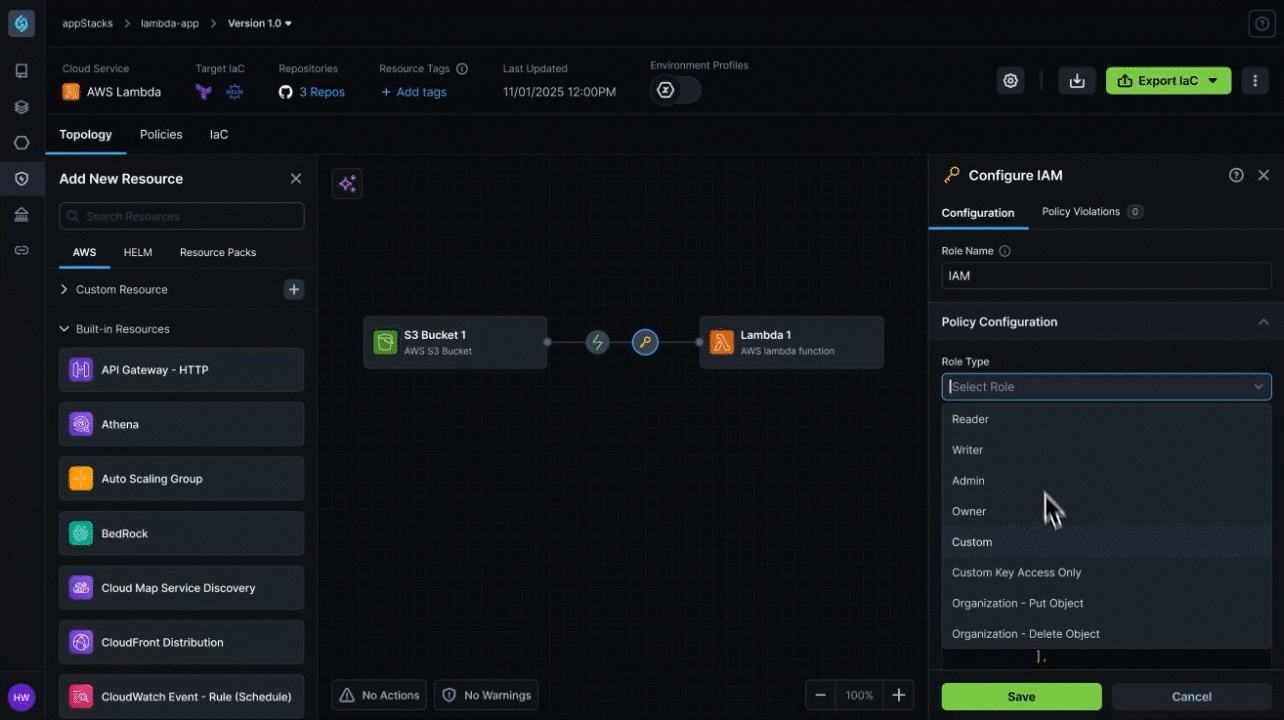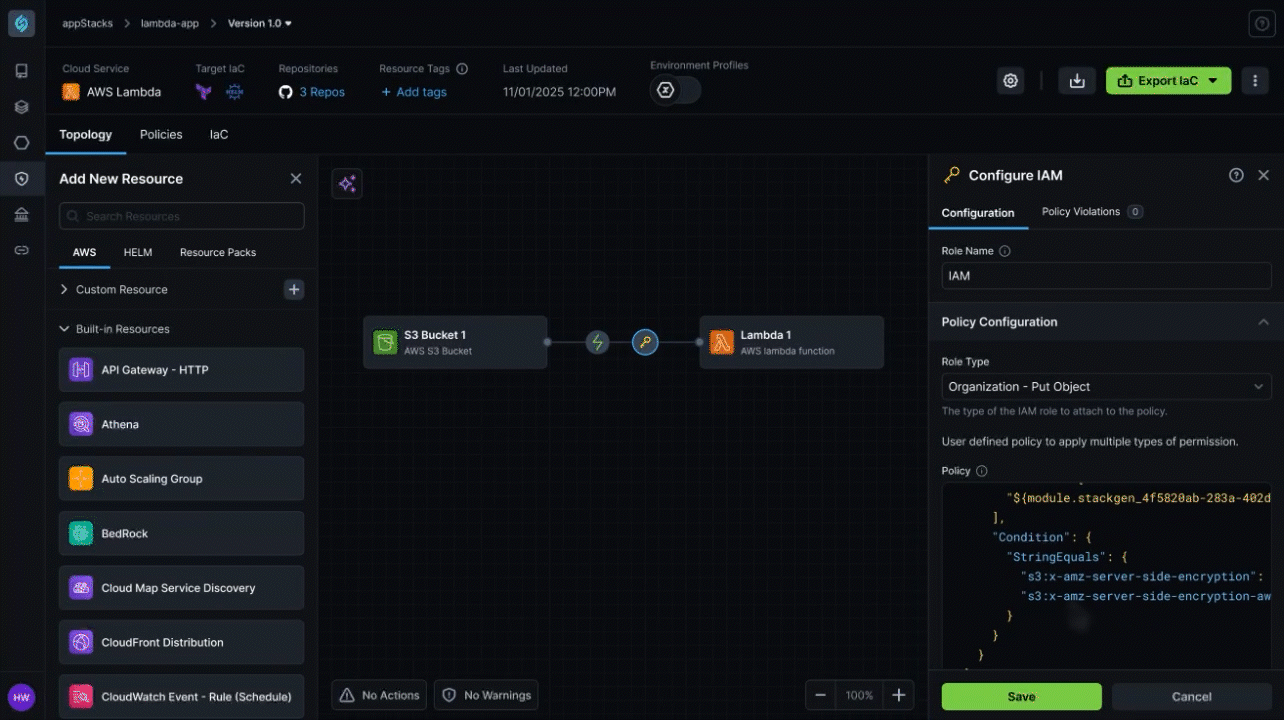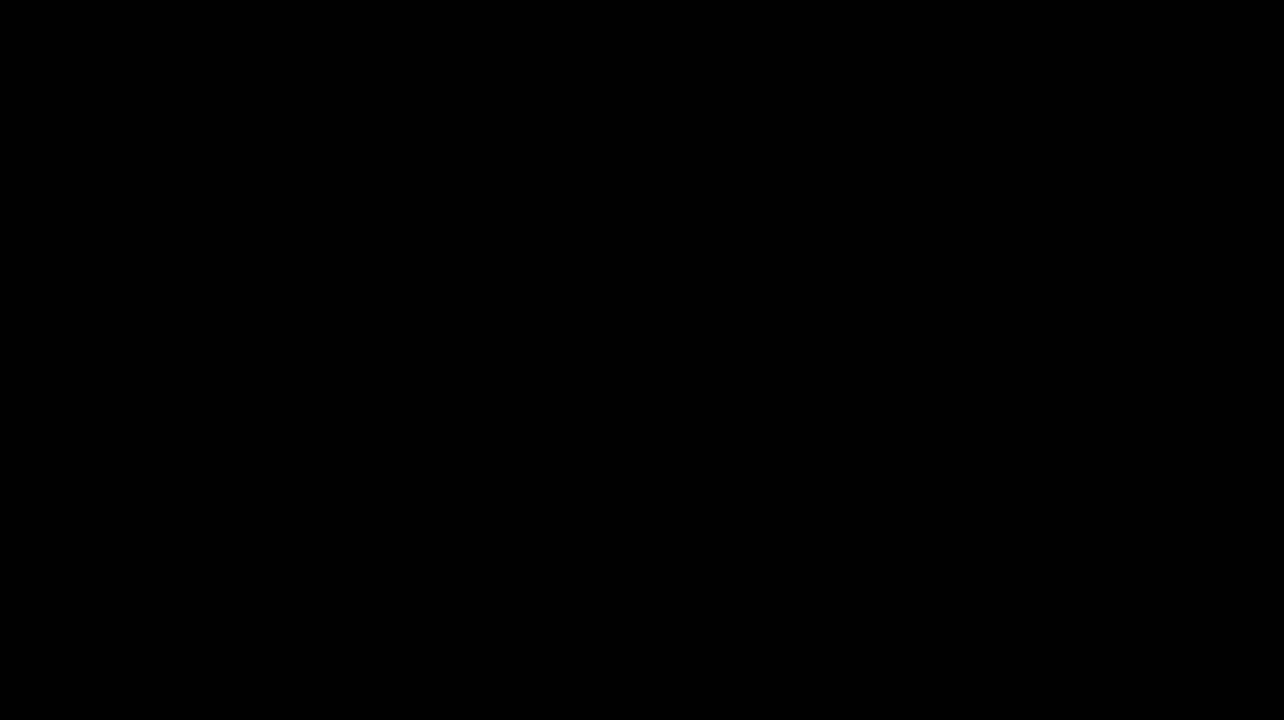
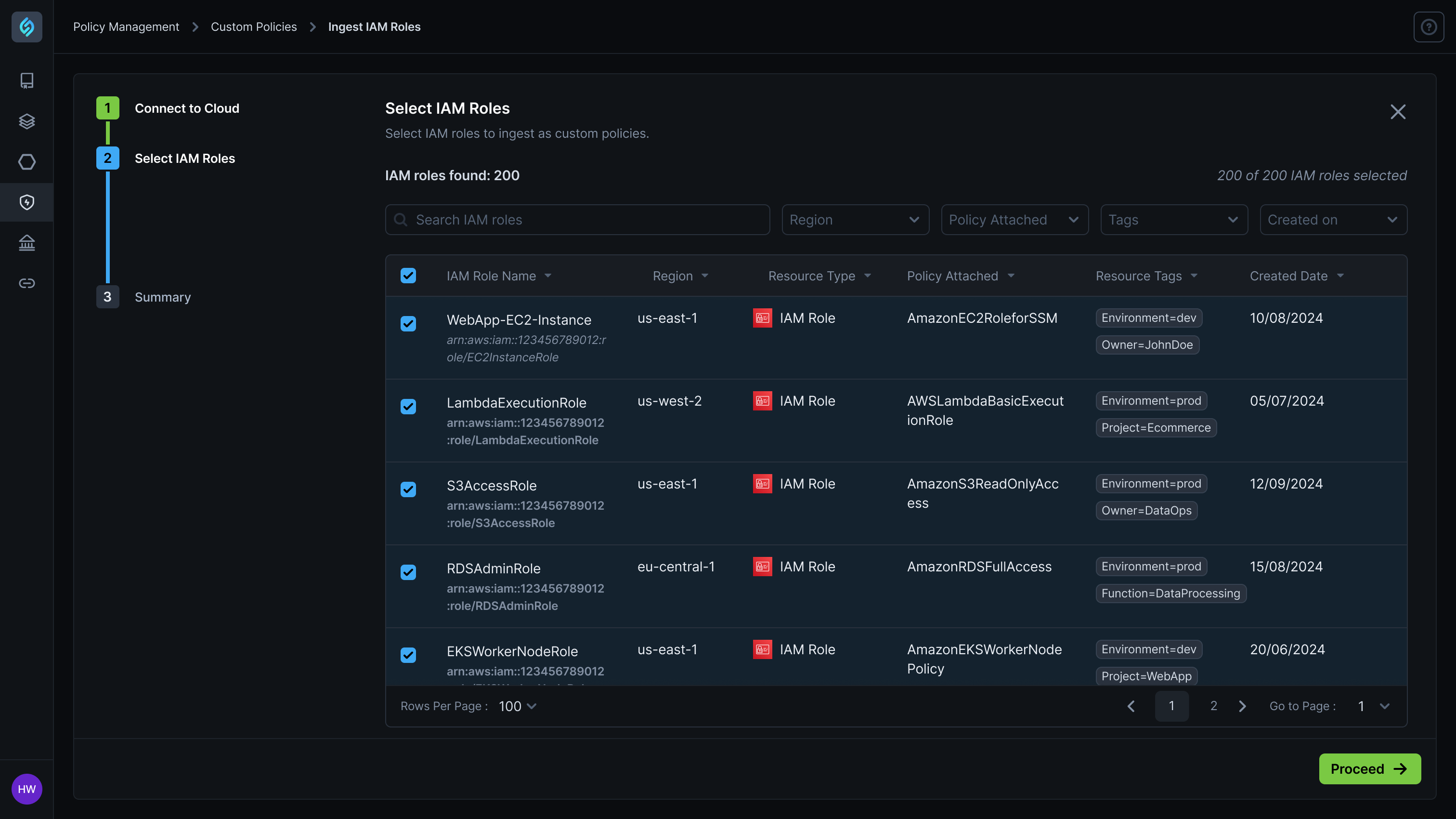
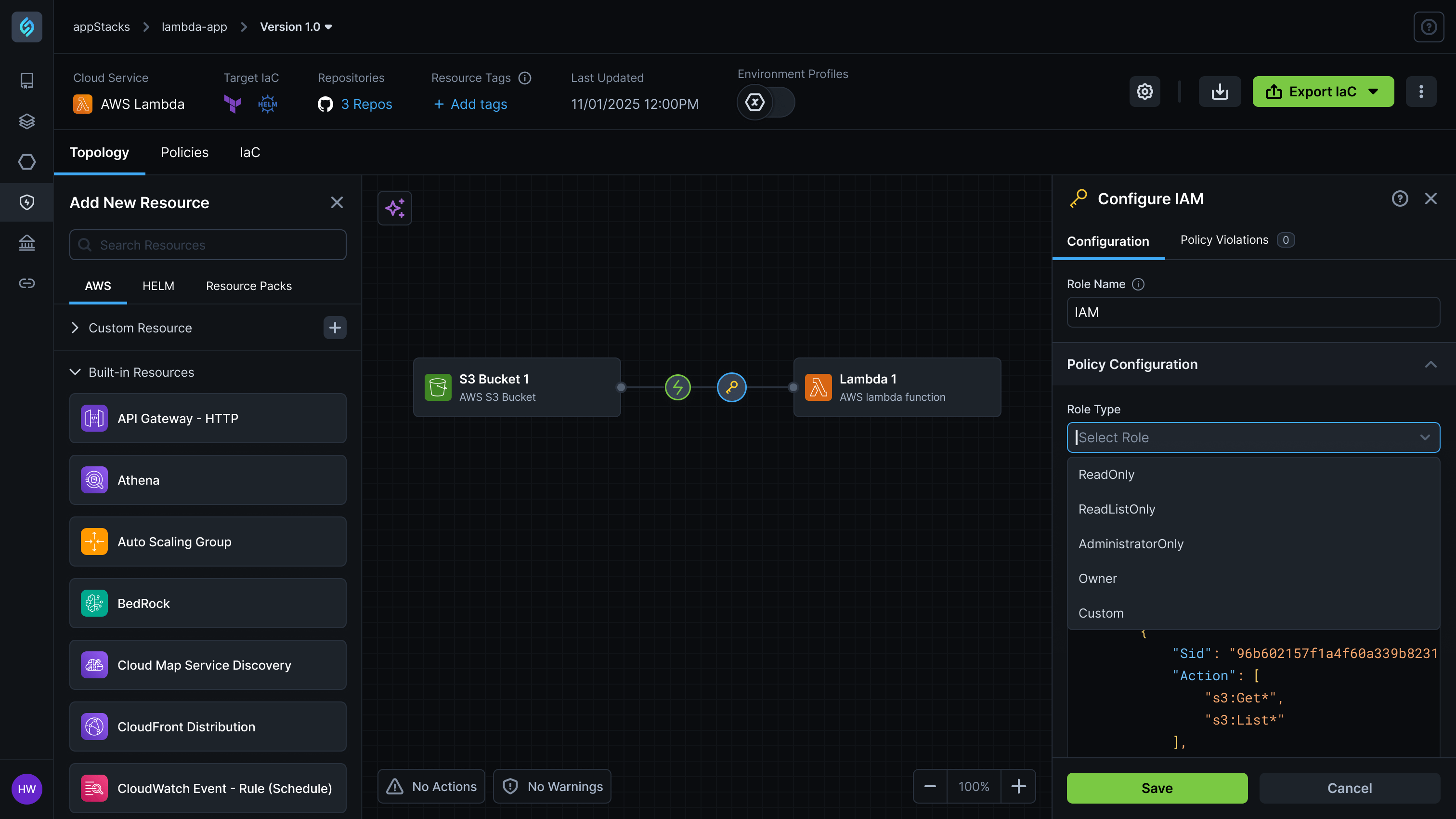
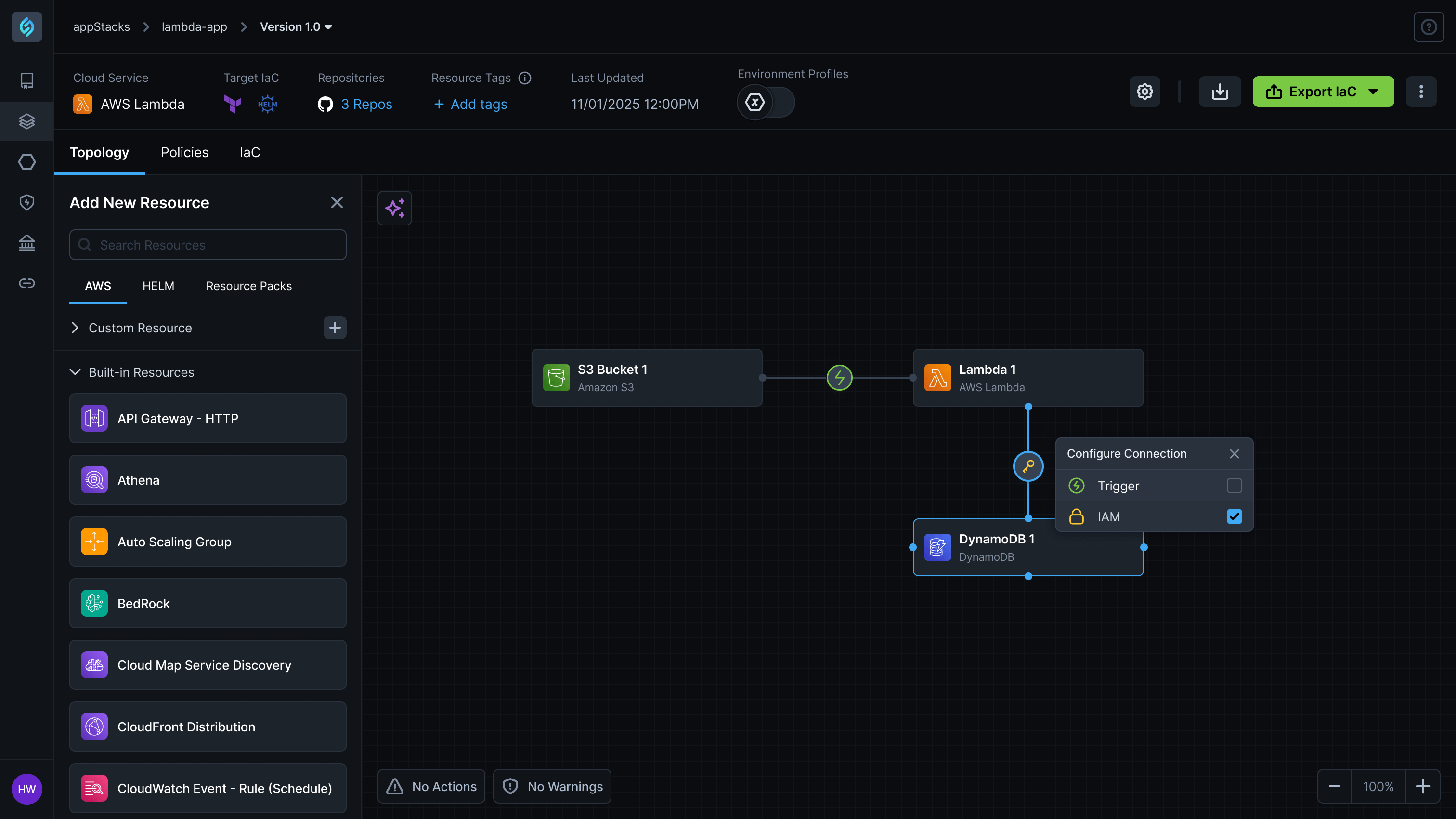
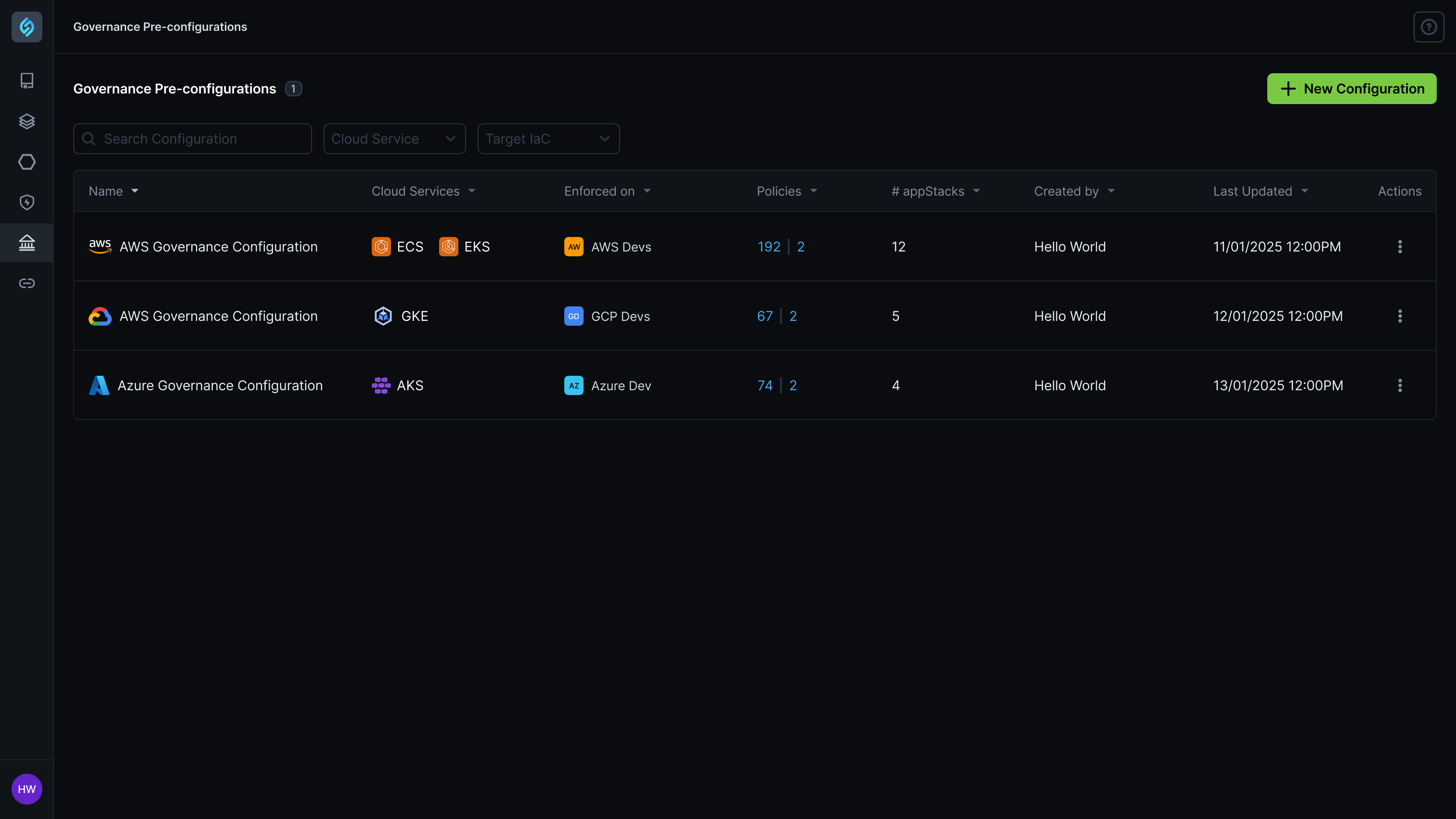
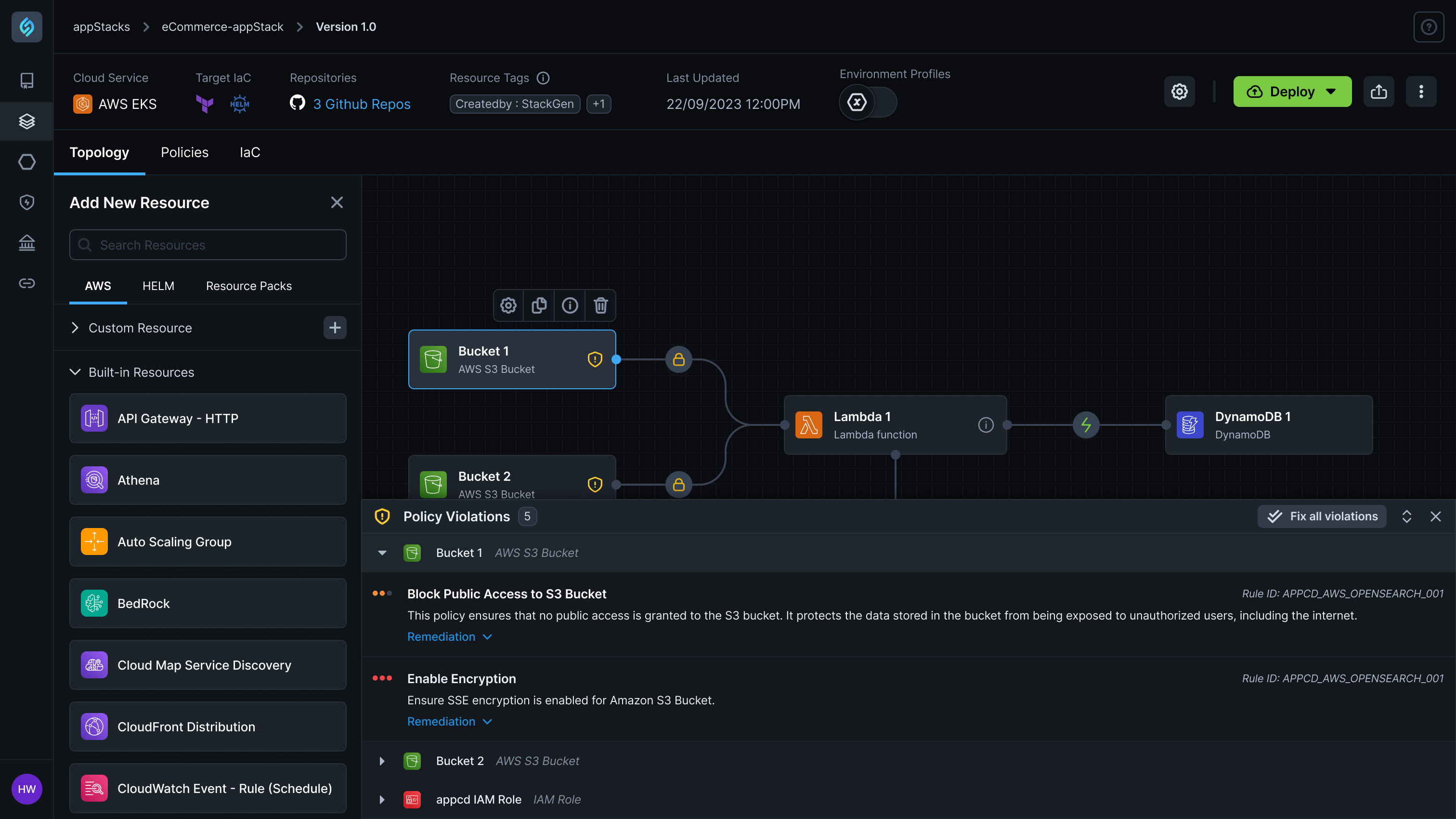
Manual IAM Configuration Creates 75% Deployment Permission Failures
Organizations struggle with complex IAM role and policy management where platform engineering teams must manually configure deployment roles, service accounts, and least-privilege access policies, leading to 75% of deployment failures due to missing permissions like ECS service creation or IAM PassRole rights, while forcing developers to wait for platform teams to manually troubleshoot and fix IAM policy issues that can take hours to resolve.